Search results
- output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to...48 KB (7,844 words) - 09:19, 15 May 2024
- A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...48 KB (6,228 words) - 22:13, 24 May 2024
- Number sign (redirect from Hash sign)symbol # is known variously in English-speaking regions as the number sign, hash, or pound sign. The symbol has historically been used for a wide range of...43 KB (4,419 words) - 14:17, 4 June 2024
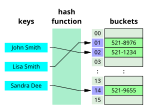
- In computing, a hash table, also known as a hash map or a hash set, is a data structure that implements an associative array, also called a dictionary...52 KB (5,873 words) - 03:14, 4 June 2024
- SHA-1 (redirect from SHA-1 hash)cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest...51 KB (5,762 words) - 12:45, 20 May 2024
- Merkle tree (redirect from Tiger-Tree Hash)the above picture hash 0 is the result of hashing the concatenation of hash 0-0 and hash 0-1. That is, hash 0 = hash( hash 0-0 + hash 0-1 ) where "+" denotes...15 KB (1,787 words) - 10:01, 19 May 2024
- Hash browns, also spelled hashed browns and hashbrowns, are a popular American breakfast dish consisting of finely julienned potatoes that have been fried...7 KB (632 words) - 10:08, 25 April 2024
- HMAC (redirect from Keyed-Hashing Message Authentication)cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of...19 KB (2,305 words) - 19:35, 1 June 2024
- Cannabis edible (redirect from Hash brownie)are an easier, more convenient way of administering products. One form of hash oil Making cannabutter Cannabis oil, or canna-oil, is a product that combines...36 KB (3,488 words) - 04:09, 14 May 2024
- C Sharp (programming language) (redirect from C hash)C# (/ˌsiː ˈʃɑːrp/ see SHARP) is a general-purpose high-level programming language supporting multiple paradigms. C# encompasses static typing,: 4 strong...97 KB (8,242 words) - 10:52, 2 June 2024
- The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S...3 KB (464 words) - 12:44, 20 May 2024
- Hash oil or cannabis oil is an oleoresin obtained by the extraction of cannabis or hashish. It is a cannabis concentrate containing many of its resins...33 KB (3,440 words) - 23:01, 1 May 2024
- A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table. Key–value pairs are stored in a DHT, and...35 KB (4,123 words) - 04:47, 9 May 2024
- Message authentication code (redirect from Keyed hash function)integrity code (MIC), and instead using checksum, error detection code, hash, keyed hash, message authentication code, or protected checksum. Informally, a...15 KB (1,781 words) - 08:44, 18 April 2024
- Associative array (redirect from Hash array)associative arrays. The two major solutions to the dictionary problem are hash tables and search trees. It is sometimes also possible to solve the problem...24 KB (2,769 words) - 18:44, 13 May 2024
- cryptography, Whirlpool (sometimes styled WHIRLPOOL) is a cryptographic hash function. It was designed by Vincent Rijmen (co-creator of the Advanced Encryption...11 KB (1,054 words) - 03:57, 19 March 2024
- Key derivation function (redirect from Password hash)passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys...13 KB (1,625 words) - 17:56, 8 March 2024
- a checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions"....10 KB (280 words) - 12:03, 21 May 2024
- blessed hash crytographic hash distributed hash table hash algorithm hash brown hash brownie hash browns hash buster hash code hash coding hash collision
- 2270622Aunt Caroline's Dixieland Recipes — Meats1922Emma McKinney SOUTHERN HASH 4 raw potatoes, ¾ cup of water, 2 green peppers, 1½ cups cold chopped beef
- Running (redirect from Hash House Harriers)runs are held in many cities and some rural areas at all tines of the year. Hash House Harriers. This is a running club that originated among expats in South-East
- i++) { hash += key[i]; hash += (hash << 10); hash ^= (hash >> 6); } hash += (hash << 3); hash ^= (hash >> 11); hash += (hash << 15); return hash; } The